Hello Readers! Today's walk through on Anthem CTF machine from TryHackMe . The room is simple and fun, it contained basics on Windows System penetration testing and privilege escalation. Let’s just jump into the box.

First thing that we always have to do is connect your machine with tryhackme network through VPN.
Let’s wait for 2-3 mins as it will take some times to boot up and then check if the ping is working or not, make sure you get the reply from the machine before starting scanning or enumeration.
Today, I introduced one similar new scanning tool called rustscan and also faster than the nmap. The nmap is also bind with it but 1st it will gives you only port details and than it will automatically start nmap scanning with advanced parameter which will help us to find more details.
rustscan <IP>
Once the machine is up and you get the proper response. Launch the rustscan with bind nmap scan.

Here I found all open port with no details, this will help you if you aware about all ports details which port is used which services.
Warning: This scan is faster but it will slow down your target system during scanning. This process doesn't harmful but slow down your speed during scanning.

After running rustscan , I got multiple ports. Let’s go for port 80/TCP HTTP.

After checking web page result, it seems like some company named as Anthem blogger website. There are 2 blogs available. Before moving forward, let’s go with directory enumeration with gobuster which is a very common practice.

Here I can find some interesting directory list as shown in snapshot.
If you check this Anthem machine it has some tasks to complete, so I can surf more like web analysis. During this I found some interesting flags value as check in mentioned snapshots.
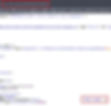
You can note it down for completing given task number 1 which is website analysis.

Found flag value

Found another flags values

During website analysis I found some interesting poem.

I wonder who is the author of this poem so I take help from google and I found one who wrote this.
So I took name and make a note.
Solomon Grundy - SG

I also observe that in website there are mail ID available from the name Jane Doe. It has mail id - JD@anthem.com
Let's make this for Solomon Grundy - SG@anthem.com
Let's check this,
http://<IP>/robots.txt
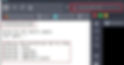
Looks like it has some useful information, let just save the above UmbracoIsTheBest! and also visit rest of the pages 1 by 1 and see if there is any clue available.
http://<IP>/umbraco gives the login page of the website but as of now we don’t have anything useful. Nothing important on rest of the 3 links.
So now Solomon Grundy. Let me try to login on Remmina RDC(Remote Desktop Client) with these details. Name as SG and password as UmbracoIsTheBest!
Accept the certificate.
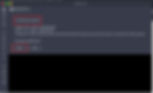
And BOOM ! I got successfully enter the system with user SG.
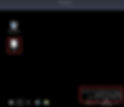
After login user.txt, shows it is available at the desktop only.

Let me enumerates more to find the Administrator access.
Let me enable hidden access.

Check the C drive and hidden file and folders. There is one backup folder, seems interesting.

There is a file restore.txt
Let me open this...

File inside the backup doesn’t have permission.
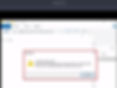
Let me try to change the permission and give full permission to the SG user.
Steps to change the permission.
Right click on file -> go to properties -> Security tab -> Advance security. here you can find the permission details.
Step1:
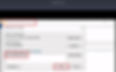
Step2:

Step3:
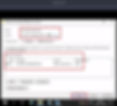
Now I have the access to the restore.txt file. Here I got one more text value, I think this could be password of Administrator account.

Let me try to use this password to login into Administrator directory.

Finger Crossed And Pray !!
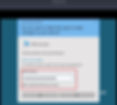
Hurray!!!

I am successfully logged in with Administrator and I also get the root.txt
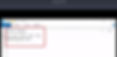
After putting all the flags values and information, I have successfully finished this room.

Thanks for reading this and I hope you liked this blog.
Happy Learning!!!
